Introduction
Imagine a digital world where your personal information is under your control(decentralized identity) – no centralized servers, no worries about endless data breaches. Sounds liberating, doesn’t it? welcome to the world of decentralized identity, where you retain complete sovereignty over your digital identity. Today we’ll talk about what decentralized identities are, how they work, what’s the difference between identity tokens vs. access tokens, and how this technology can take your online security and convenience to new heights. So let’s get started!
Table of Contents
What is decentralized identity?
Decentralized identity (self-sovereign identity, SSI) is a new paradigm where individuals have full control over their digital identity, without the intervention of any middleman. In traditional identity systems we store data across multiple centralized servers—banks, social platforms, government portals—including:
- single point of failure: If a server gets hacked, your data may be leaked across multiple services.
- Limited Control: Users did not have the power to decide the use-case of their data.
- Redundant KYC: You have to submit documents again and again, wasting time and frustration.
Decentralized identity solves these problems by empowering users to:
- User-Centered Ownership: Personal data is safe in your digital wallet (mobile or hardware).
- Verifiable Credentials: Trusted issuers cryptographically sign credentials, which you present like a digital badge.
- No Central Authority: Verification occurs on a distributed ledger (blockchain)—tamper-proof, transparent, and reliable.
“My money is safe in my bank, my identity data should also be in a safe place.”
Why does traditional identity diminish?
Emotional Despair:
- Manuela felt like submitting her address proof again and again – railway reservation, Netflix, telco service.
- The “Upload your ID” prompt for every new service made us tired of digital identity.
Data breach nightmare:
- The 2017 Equifax breach leaked the sensitive data of 145 million Americans, leading to a 34% increase in identity theft cases.
- Recently KYC service has hacked the dark web pay list containing information of banking customers.
Lack of interoperability:
- Rajesh has Paytm KYC, Zerodha KYC, SBI KYC – three different processes, three different wait times.
- Data redundancy leads to wasted time, user dissatisfaction, and high compliance costs for businesses.
Decentralized identity is a holistic, scalable, and user-friendly solution to solve all these issues.
Main components of SSI ecosystem
Understanding the building blocks helps to see the whole picture:
1. Decentralized Identifier (DID)
- Unique, blockchain-registered identifier (e.g., Did:Example:123ABC).
- The DID document contains the public keys, service endpoints.
- Globally solvable—any validator can bring in and verify.
2. Verifiable Credentials (VC)
- Tampering with clear digital credentials issued by trusted entities (universities, government agencies).
- Use the W3C VC data model—credential subject, issuer, certificate.
- Stored in the user’s wallet; Presented selectively.
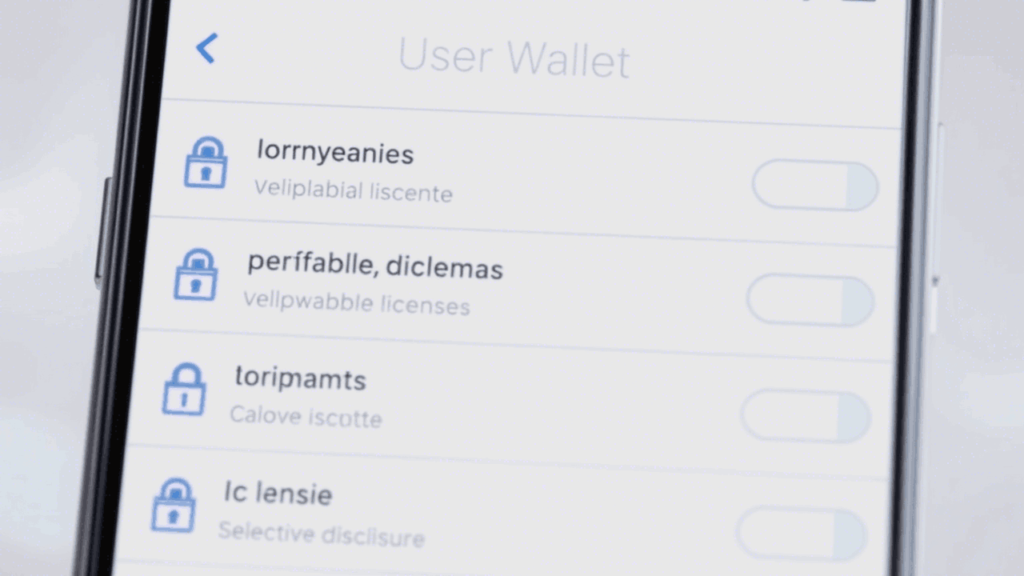
3. Digital Wallet
- Secure apps (mobile/desktop) to store DIDs and VCs.
- Support key management, backup, selective disclosure.
- UX-friendly interface increases adoption.
4. Distributed Ledger/Blockchain
- Host DID registries, revocation registries, audit logs.
- Ensures immutability and decentralization.
- Not data-heavy – only cryptographic proofs, no personal data.
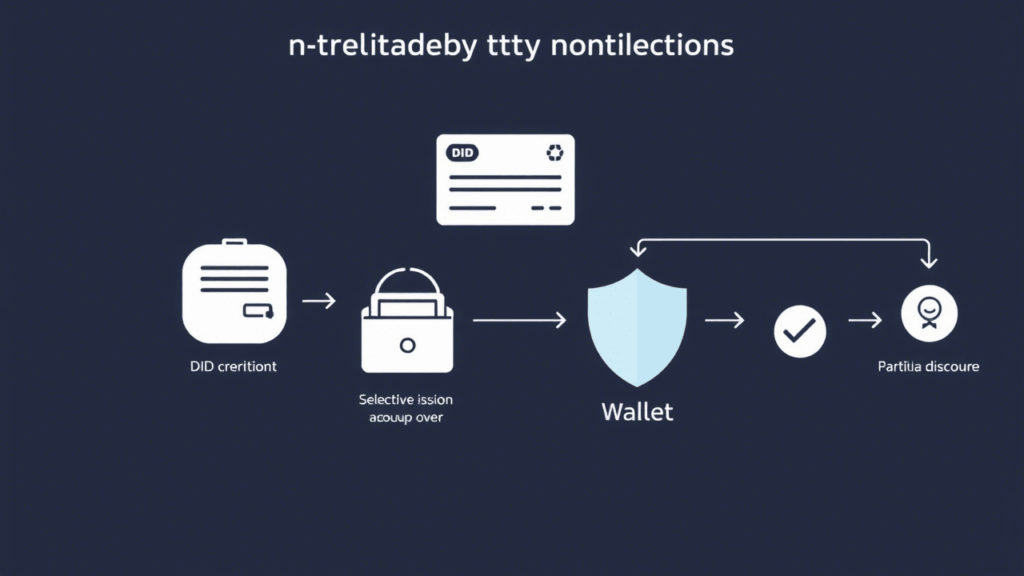
How does decentralized identity work
| step | Description |
| 1. created | User creates wallet public/private key pair, publishes DID document on the ledger. |
| 2. Issuing Credentials | The issuer verifies the identity (personal or digital), signing a verifiable credential. |
| 3. Wallet Storage | The user receives VC and stores it in his wallet with encryption. |
| 4. Selective Disclosure | The user selects specific claims (e.g., over 18 years of age) to share with the verifier. |
| 5. Verification | The verifier receives the issuer’s DID document, checks the cryptographic proof and revocation status. |
Comment: The actual personal data never reaches the blockchain – only evidence and metadata.
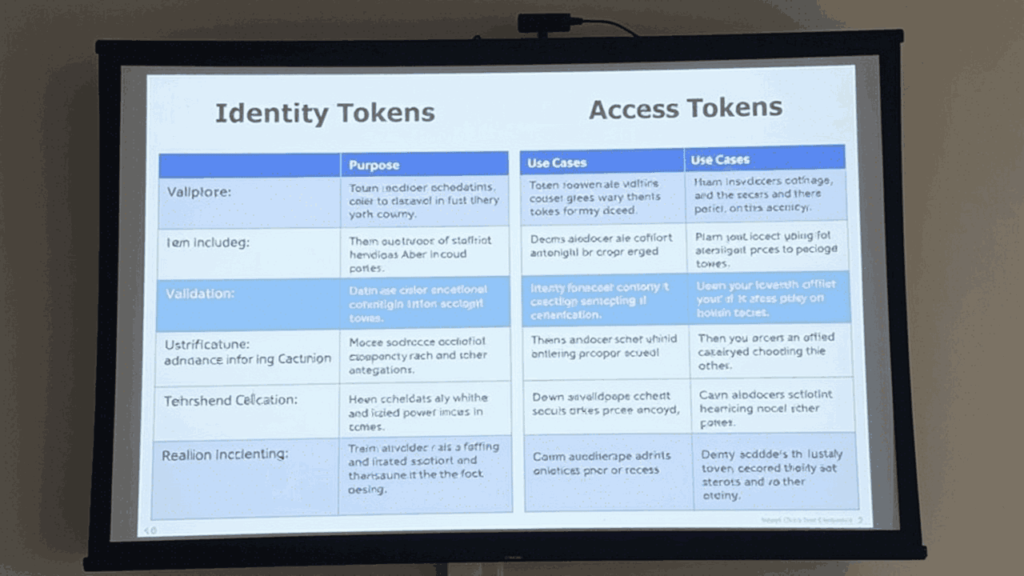
Identity Token vs Access Token
Authentication systems often confuse these; Clarity matters for security and UX:
| Speciality | identity token | access token |
| Objective | User identity (who they are) | Rights to grant resource access to the user (what they can do) |
| Format | with JWT id_token Claim | with JWT/opaque access token Claim |
| Contents | Profile information (name, email, sub) | Scope, Permissions, Resource Server Reference |
| end of printing | Medium age (for example, 1 hour) | Short lived (for example, 15 minutes), refreshable |
| use | Personalizing the UI (“Hello, Ayesha”) | Access to API (Authority: Carrier…) |
| Safety Tips (Best Practices) | Store in secure cookie, not localStorage | Keep in memory or safe storage, rotate frequently |
Deep Dive: ID Token vs Access Token
- Login and Session Management
- ID token: Continued on successful login; Read by the client to display user information.
- access token: Sent with every API call; The server verifies and grants access based on scope.
- ID token: Continued on successful login; Read by the client to display user information.
Example flow:
Basic lesson
copyedit
User → Auth Server: /authorize?scope=openid Profile Email
Auth Server → Client: id_token + access_token
Client: display username from id_token
Client → API: GET /user/data Authorization: bearer access_token
API: Validate token signature, scope, expiration → Serve data
- Security Considerations:
- Always validate the token signature against the issuer’s JWKS.
- check Aud (audience) and ISS (Issuer’s) claim.
- Implement token revocation lists (for protocols).
- Always validate the token signature against the issuer’s JWKS.
Key Benefits of Decentralized Identity
- Privacy and Minimal Disclosure
- Share only required information – Claim “over 18” for age verification.
- Zero-knowledge proofs enable claims to be validated without disclosing raw data.
- Share only required information – Claim “over 18” for age verification.
- enhance security
- Eliminate centralized honeypots; Mitigate large-scale data-breach risks.
- Cryptographically verifiable, tamper-resistant credentials.
- Eliminate centralized honeypots; Mitigate large-scale data-breach risks.
- User Experience and Efficiency
- One-click KYC across multiple services.
- No need to fill forms again and again – login once, access everywhere.
- One-click KYC across multiple services.
- cost savings for businesses
- Reduction in KYC/AML infrastructure and personnel costs.
- Lower attrition increases customer onboarding rates by up to 30%.
- Reduction in KYC/AML infrastructure and personnel costs.
- regulatory compliance
- GDPR, CCPA compliant—users control data sharing, consent trails are auditable.
- Audit logs are stored immutably on the ledger.
- GDPR, CCPA compliant—users control data sharing, consent trails are auditable.
Implementation Roadmap for Enterprises
| phase | action items |
| 1. Strategy and planning | • Identify business cases (e.g., KYC, employee ID)• Create cross-functional SSI teams |
| 2. Technology Selection | • Evaluate Frameworks: Hyperledger Indie, Sovrin, Uport, Ceramic• Pilot Mini MVP |
| 3. Infrastructure Setup | • Deploy DID registry (public or consortium blockchain)• Set Revocation Registry |
| 4. Wallet and API Development | • Build user-friendly wallet apps• to integrate did-jwt, veramo Library |
| 5. Issuer and Validator Onboarding | • Partnership with universities, banks, government agencies to issue credentials• Establish verification endpoint |
| 6. Pilot and Feedback Loop | • Launch the pilot with the selected user group• Collect user feedback, iterate on UX |
| 7. Scale and governance | • Define governance policies• Scale to a wide user base• Continuous monitoring |
Emotional touchpoints: Teams are often hesitant because of perceived complexity – start with a narrow use case (e.g., employee ID), show quick wins, then expand.
Real-world use cases and anecdotes
- higher education certificate
- The university issues digital degree credentials. Students share with employers instantly.
- Anecdote: Priya got 5 job offers in 2 weeks – previously degree verification took 2-4 weeks per employer.
- The university issues digital degree credentials. Students share with employers instantly.
- cross border finance
- Crypto exchanges require KYC – users present government-issued VC without uploading raw SSN.
- Faster onboarding and enhanced privacy for high net worth investors.
- Crypto exchanges require KYC – users present government-issued VC without uploading raw SSN.
- Health care
- Patient vaccination records stored as VC. At travel checkpoints, only vaccine status proof is shared.
- Reduces the risk of counterfeit documents; Speeds up verification.
- Patient vaccination records stored as VC. At travel checkpoints, only vaccine status proof is shared.
- supply chain
- Manufacturers issue product origin certificates in the form of VC. Retailers and consumers verify authenticity on the spot.
- Reduces counterfeiting and builds brand trust.
- Manufacturers issue product origin certificates in the form of VC. Retailers and consumers verify authenticity on the spot.
- smart city
- Citizens use SSI wallet for public transport passes, library membership, municipal services.
- The pilot for the city of Barcelona reduced administrative overhead by 25%.
- Citizens use SSI wallet for public transport passes, library membership, municipal services.
“SSI has democratized our citizen services – now everyone gets equal access without compromising privacy,” Barcelona’s CIO explains.
Challenges and Mitigation Strategies
| challenge | Mitigation |
| User education and adoption | • Simple, intuitive wallet UX• Interactive tutorial, in-app guidance |
| interoperability standards | • Adopt W3C standards (DID Core, VC Data Model)• Participate in consortium for alignment |
| Key Management and Recovery | • Hardware wallet option• Social recovery mechanism (trusted contacts) |
| Governance and legal framework | • Multi-stakeholder governance board•Regulatory sandbox for compliant use |
| Scalability and Performance | • Use permitted ledgers for high volume use cases• Off-chain storage of bulk data |
Emotionally, businesses worry about “what if something goes wrong?” – Clear governance and recovery plans build confidence.
Future trends in decentralized identity
- Decentralized Web (Web3) integration: SSI wallets become the login mechanism for DApps, NFTs, DeFi platforms.
- Verifiable Submissions for AI: AI services verify user claims before providing personalized experiences.
- Data Monetization Model: Users selectively monetize their data (for example, market research) and earn micropayments.
- Biometric-supported decentralized ID: Multi-factor DID combining hardware tokens, biometrics, and cryptography.
- RegTech Applications: Automated compliance through smart contracts – real-time KYC/AML checks without manual intervention.
“This is just the beginning – the SSI revolution will redefine digital trust over the next decade,” Industry analyst Arjun Mehta’s prediction.
FAQ Section
What is decentralized identity and why does it matter?
Decentralized identity shifts control away from centralized authorities to the users themselves, thereby enhancing privacy, security, and user experience. This matters because centralized systems are prone to data breaches and user frustration.
How are identity tokens different from access tokens?
identity token (id_token) prove who you are and include profile claims, while access tokens (access token) Provide permission to interact with protected APIs. Separating them imposes clear security limitations.
Can I lose access to my decentralized identity wallet?
Yes—if you lose your private keys without a backup, you may lose access permanently. Mitigation strategies include encrypted backups, hardware wallets, and social recovery
Are SSI solutions compatible with existing OAuth/OIDC infrastructure?
Many SSI frameworks provide adapters for hybrid deployment, enabling gradual migration without replacing the entire authentication stack.
What rules govern decentralized identity?
Although no SSI-specific legislation exists yet, implementation will need to comply with GDPR, CCPA, and emerging data privacy regulations. Ongoing regulatory sandboxes help shape the future framework.
How does selective disclosure protect user privacy?
Selective disclosure (via zero-knowledge proofs) allows users to prove specific characteristics (e.g., age) without revealing sensitive data (e.g., exact date of birth).
Is blockchain necessary for decentralized identity?
A distributed ledger or permissioned blockchain is commonly used to register DID documents and revocation registries. However, implementations vary depending on the trust model.
Which industries benefit most from SSI?
Finance (KYC/AML), Healthcare (Patient Records), Education (Digital Diploma), Supply Chain (Product Provenance), Government Services (e-ID).
Conclusion and call-to-action
Decentralized identity is more than technology – it is a movement toward a privacy-first, user-empowered digital future. By adopting SSI, organizations streamline compliance, reduce costs, and delight users with frictionless experiences. Individuals regain control over their data and share only what is necessary when necessary.
Are you ready to transform your digital identity strategy?
- Download our free SSI Starter Kit: Step-by-step guides, code samples, and best practices.
- Register for our next webinar: “Implementation of SSI in Financial Services” on June 25, 2025.
Take the first step today—because a secure, user-centric digital world is waiting for you!
ALSO READ
Best Dividend Stocks for Passive Income 2025: Your Guide to Steady Returns

